Azure DevOps Permissions and Groups: A Complete Guide
Managing Azure DevOps permissions doesn’t have to be complicated. With the right structure, you can control access across your organization, projects, repositories, and pipelines without feeling overwhelmed.
In this guide, we’ll break down permissions step by step, show you how to configure them, and highlight best practices for keeping your DevOps environment secure.
🔑 Why Azure DevOps Permissions Matter
Permissions in Azure DevOps are the foundation of security and collaboration. Setting them correctly ensures:
Developers can contribute without unnecessary restrictions
Sensitive resources remain protected
Teams only see and modify what’s relevant to them
Administrators retain centralized control
👉 Think of it as least privilege access applied across your DevOps workflows.
🧩 Understanding Azure DevOps Security Groups
In Azure DevOps, permissions are handled through security groups. These groups determine what actions users can perform.
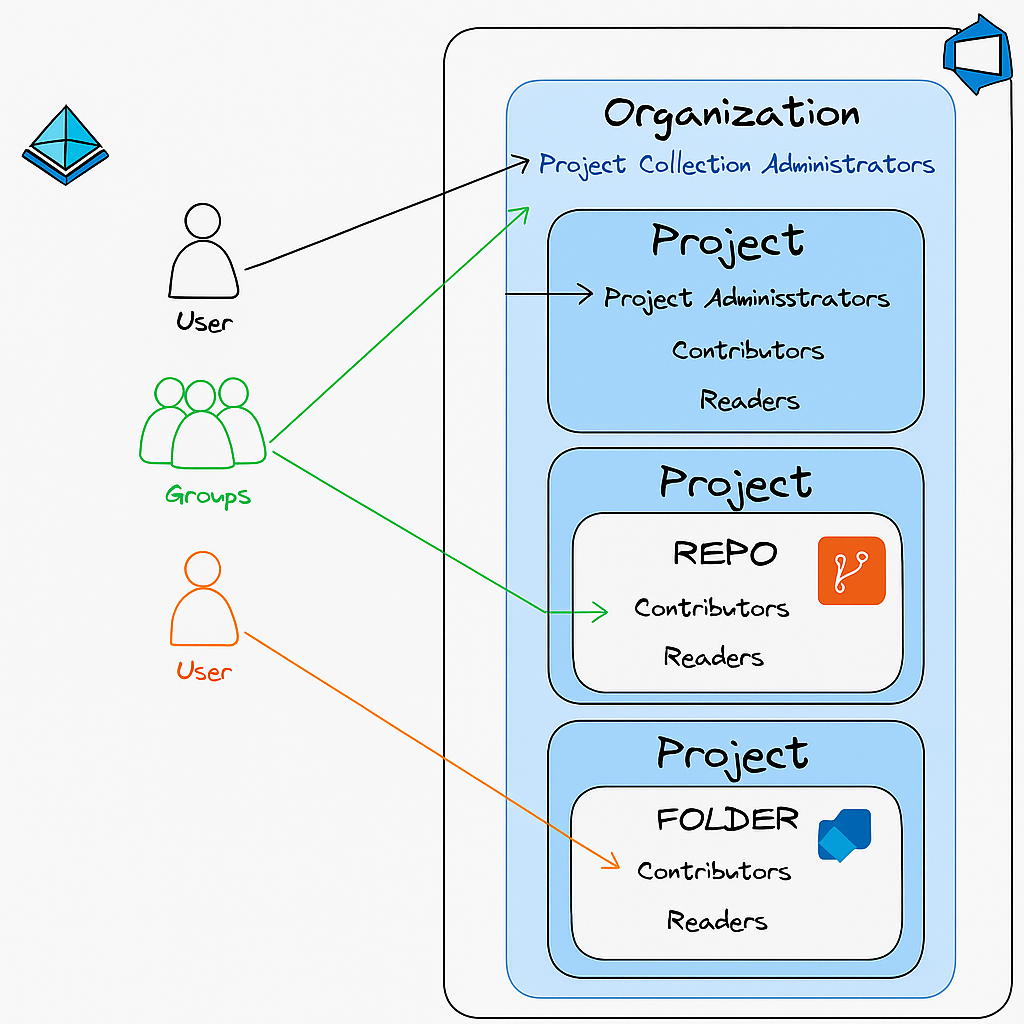
Common Group Types
Predefined groups – such as Readers, Contributors, Project Administrators, or Project Collection Administrators.
Custom groups – which you can create and configure with specific permissions.
Permission Levels
Permissions can be scoped at different levels:
Organization level – e.g., Project Collection Administrators
Project level – Readers, Contributors, Project Administrators
Repository or Branch level – fine-grained control for code access
Pipeline or Folder level – control over build and release definitions
⚙️ Configuring Permissions at the Organization Level
At the top layer, you manage access through Organization Settings.
Steps to Assign Organization-Level Roles:
Go to Organization Settings.
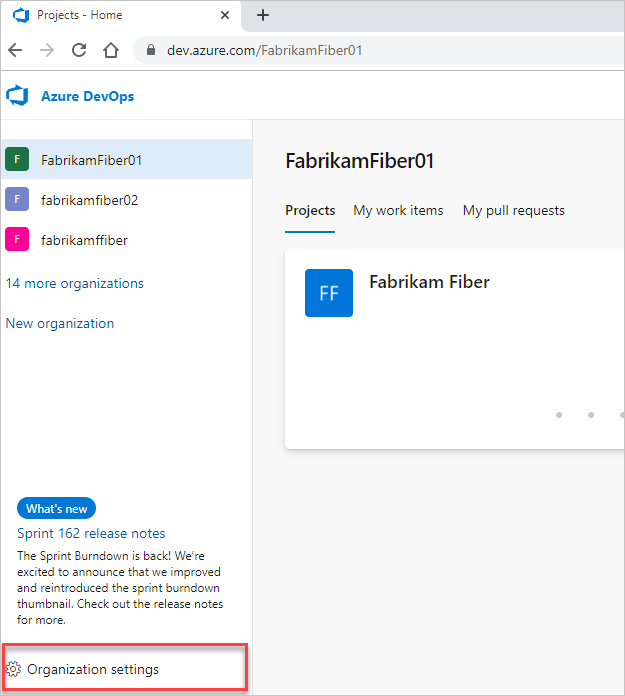
Open Permissions.

Assign users to groups such as:
Project Collection Administrators – full control across all projects
Readers / Contributors – limited but scoped access
👉 Best Practice: Use Project Collection Administrator roles sparingly. Reserve them for trusted administrators only.
📂 Project-Level Permissions
Each project comes with three main roles:
- Reader: View almost everything (code, work items, pipelines) but cannot modify
- Contributor: Create and edit code, work items, and pipelines
- Project Administrator: Full access to project settings and resources
Steps to Configure:
Navigate to Project Settings.
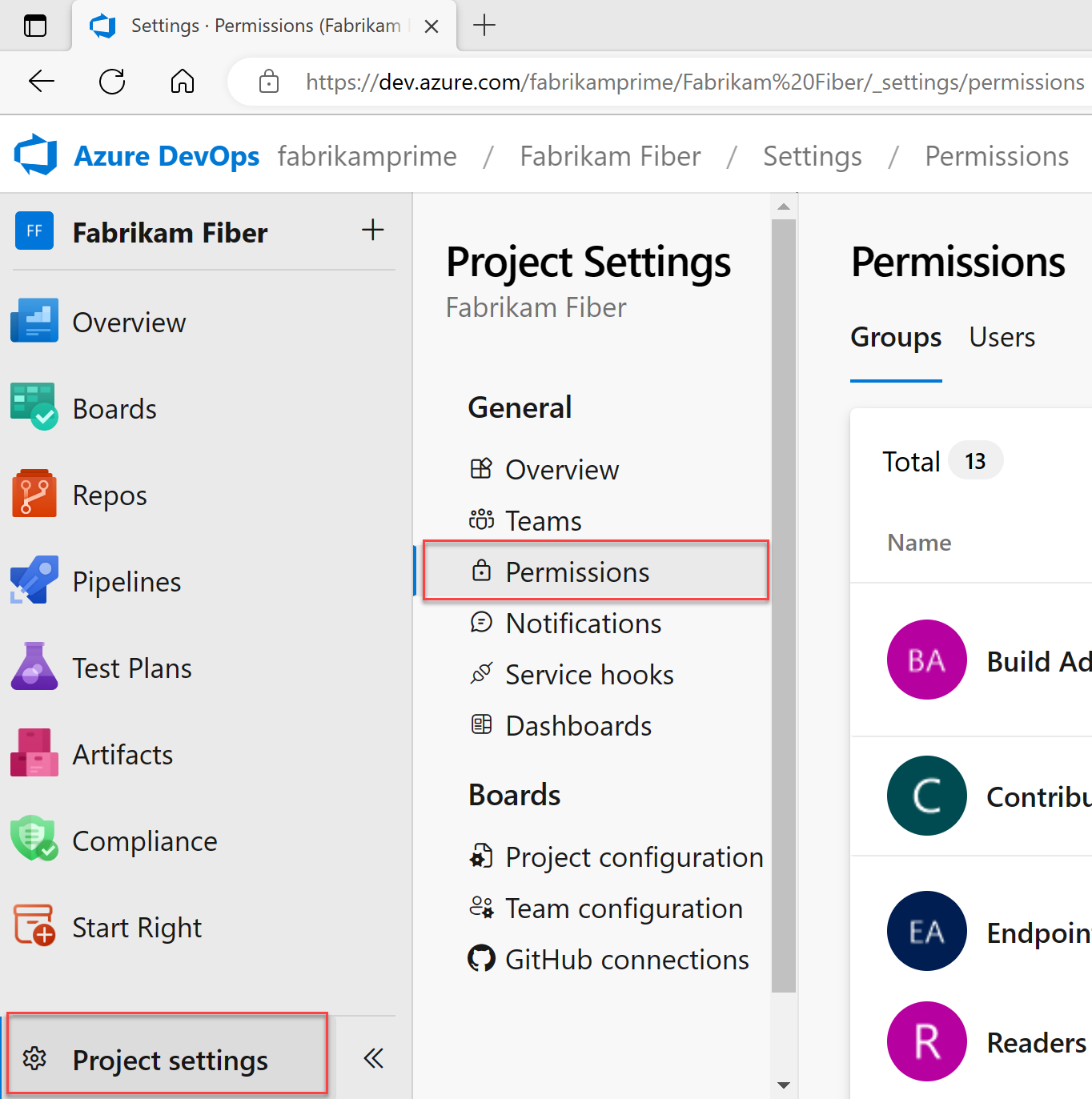
Select Permissions.
[Project-level roles overview]Add users or groups and assign the appropriate role.
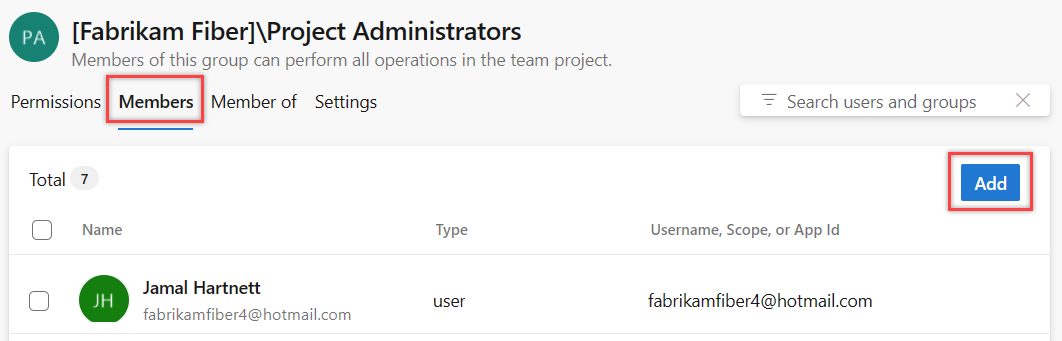
👉 Pro tip: Start everyone as Readers and grant additional access (e.g., Contributor) only where needed.
🛠️ Creating Custom Security Groups
Sometimes default roles aren’t enough. That’s where custom groups shine.
How to Create a Custom Group
Go to Project Settings > Permissions.
Click New Group.
Define the group name and description.
Assign custom permissions (e.g., repo access but no pipeline edit rights).
Add members.
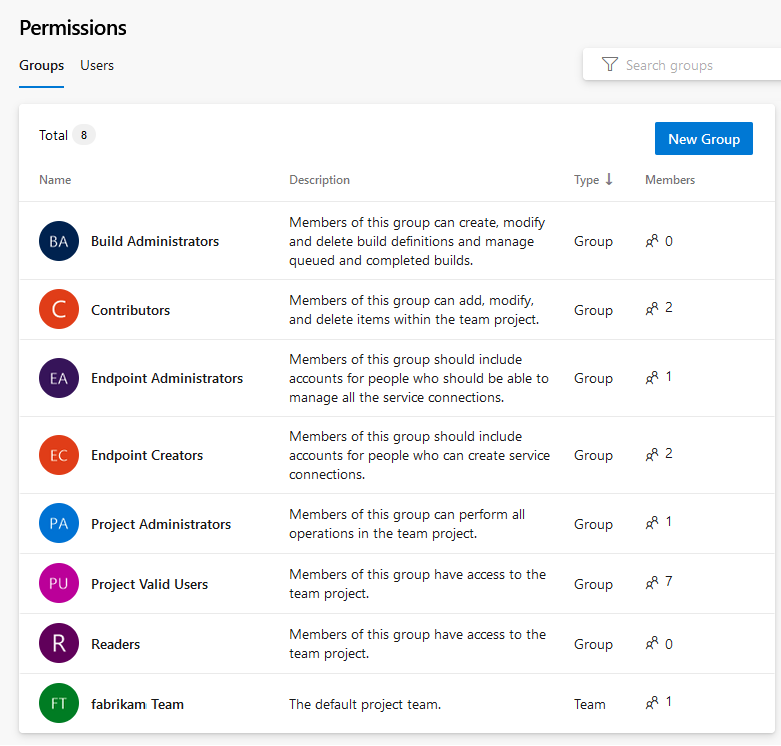
This allows you to tailor security precisely to your workflow.
🗂️ Repository and Branch-Level Permissions
For more granular control, Azure DevOps lets you set permissions at the repository or branch level.
Repository Permissions
# Example: Restrict repo access
User: dev1@example.com
Permission: Contribute
Scope: Repo – PaymentService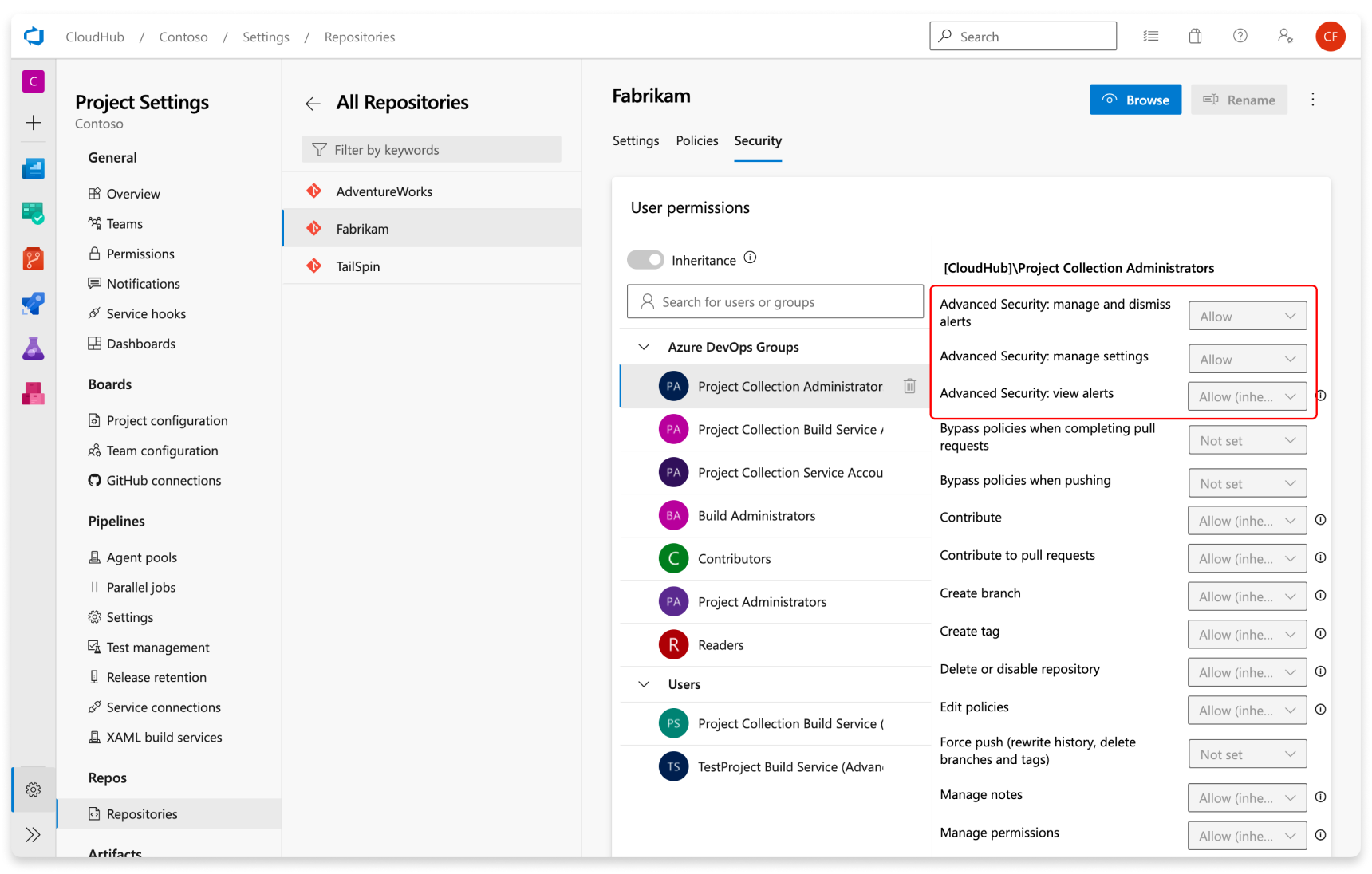
Branch Permissions
Select a repository and open the branch you want to secure.
Go to Security.
Assign roles (e.g., restrict direct pushes to
main).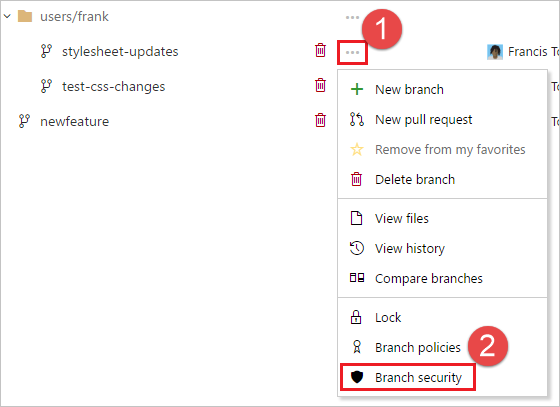
🚀 Pipeline and Folder-Level Permissions
Pipelines can also be organized into folders, making it easier to manage permissions.
Steps:
Go to Pipelines.
Organize pipelines into folders.
Open Folder Settings > Manage Security.
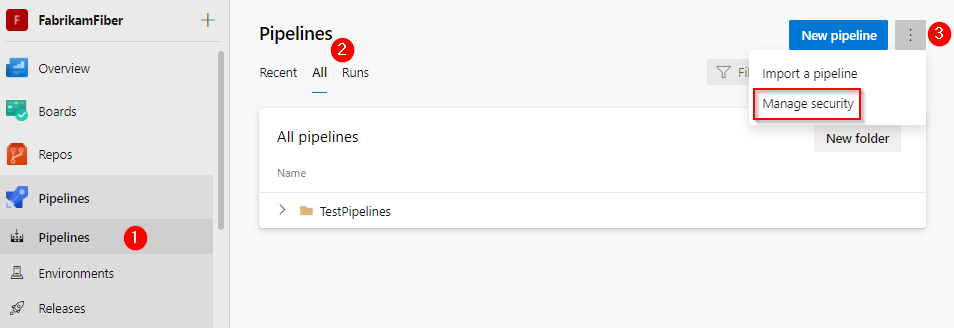
Add users or groups and assign permissions (e.g., who can run or edit pipelines).
This is especially useful for large organizations with multiple teams.
✅ Best Practices for Azure DevOps Permissions
Principle of least privilege – always give the minimal access required.
Use groups, not individuals – easier to manage at scale.
Layer permissions – Reader at project level, Contributor at repo/branch level.
Automate with code – manage permissions via scripts or Infrastructure as Code.
Review regularly – remove outdated permissions as roles change.
🎯 Conclusion
Azure DevOps permissions may look complex, but once you understand the hierarchy, they become a powerful tool for managing access securely and efficiently. By using security groups, scoped permissions, and best practices, you’ll maintain a balance between productivity and governance.